Data Security
Platform.sh lets you deliver amazing digital experiences, while keeping your site safe, secure, and available—24x7. Now you can navigate through changing requirements and updates as you’re protected against cyberattacks.
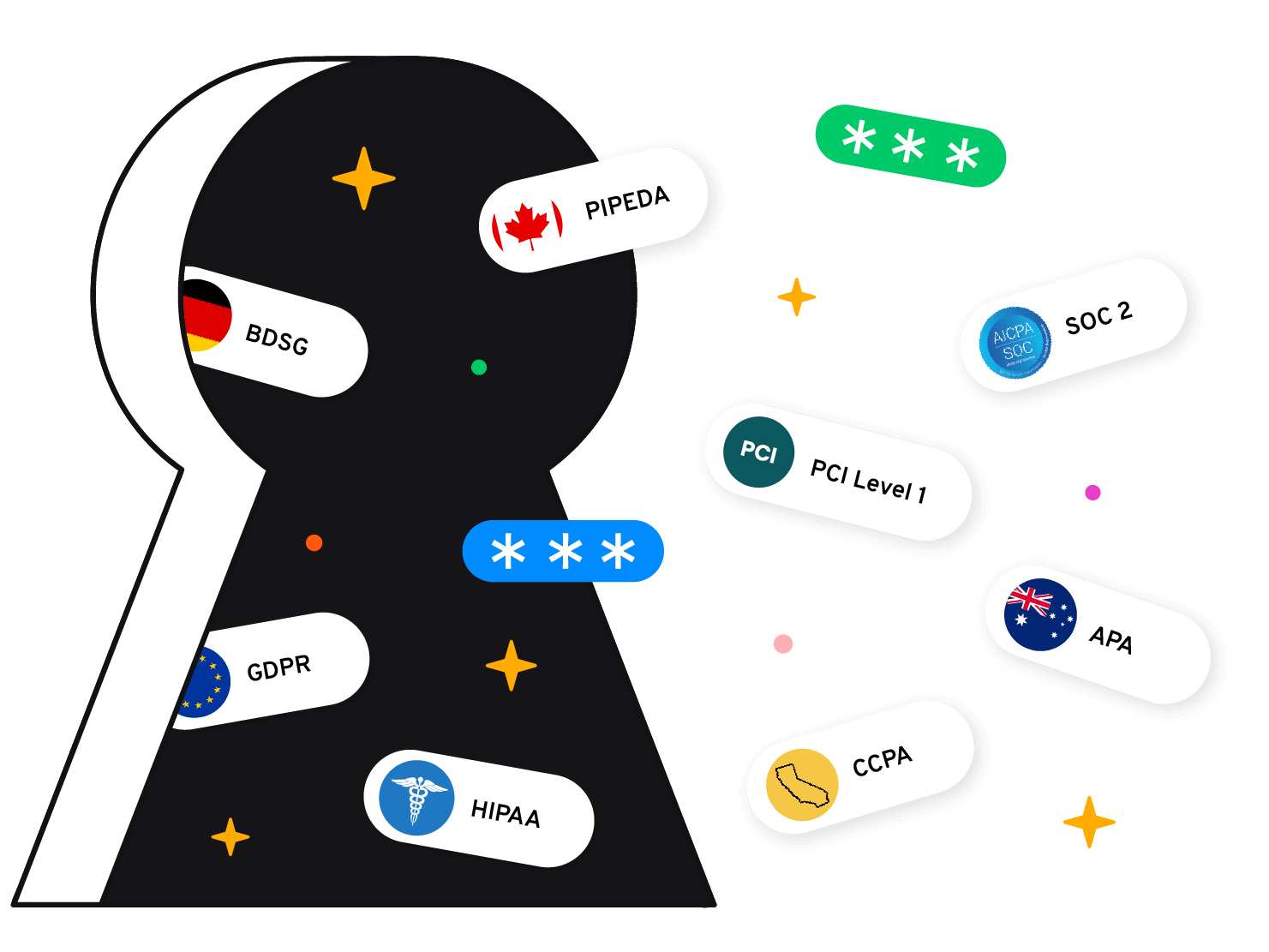
Data privacy in today's world
Platform.sh takes data security and governance seriously. We're compliant with the European GDPR (DPA available), German BDSG (DPA available), Canadian PIPEDA, and the Australian Privacy Act. We've demonstrated our commitment to data security by undergoing an annual SOC 2 Type 2 examination over Security, Privacy and Availability, and by achieving PCI DSS Level 1 compliance for our platform hosted on Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). We are also members of Gaia-X, a private-public initiative to develop common requirements for a European data infrastructure.
When you use Platform.sh, you can:
- Know that your security comes first in everything we do. We promptly notify you if we detect a breach of security. And we will never sell your data.
- Control what happens to your data. You can access it or take it out at any time.
- Know where your data is stored and rely on it being available when you need it. You define where your data is stored. We operate our service from multiple data centers with strong security practices that are independently validated by third-party auditors.
- Be confident knowing that customer data is not used for advertising. You own your data. We don't process your data for advertising purposes.
- Be reassured that our regular infrastructure vulnerability scans and penetration tests will keep our service secure.
We keep all your data private and safe
Cryptography and user security
All of our sites adhere to our cryptographic controls policy, which mandates the use of strong, industry-standard cryptographic measures. These measures include TLS for data in transit, encrypted disks, and support for 2FA.
Auto-redundant architecture
Our Dedicated offering comes with automated triple redundancy for every element of your stack, as well as automated full-cluster backups.
Security updates and stack management
Platform.sh provides security updates for every element of the stack as soon as they’re available—without service interruption.
Permissions and access management
Retain tight control and governance over user access via fine-grained, per-environment permissions.
Project and data isolation
Each project runs in isolation, with the most minimal network surface possible. Every service is network isolated from other services.
Global managed CDN
Platform.sh makes it easier to integrate your application with a CDN versus configuring all the CDN/cloud bits yourself.
Security updates and stack management
We keep your services secure, so your team can focus on building cool stuff.
Platform.sh takes over the activities needed to manage the stack and perform infrastructure security updates saving you time, frustration, and money. So you can focus your efforts on building and maintaining world-class applications.
Instant and global updates
No more outdated software and libraries. Our seamless infrastructure rollouts enable you to stay current with all the latest versions. Updating your application is simply a lightning-fast redeploy away. Do it manually or automate it to fit your change windows.
New releases as they go stable
We follow a strict testing procedure for every release of new versions of runtimes and stack components.
Git-driven architecture
Every change to your infrastructure configuration is versioned and auditable, so you can have peace of mind.
Immutable architecture
Every application is deployed to a read-only file system. Any software install or change to the application is through a secure and auditable process.
Rigorous security incident procedures
Should an infrastructure security incident occur, our dedicated security teams will provide 24/7 coverage. Engineers will be assigned and they will determine the root cause and mitigate the issue by executing our stringent incident-management process to resolution.
24/7 incident coverage
Should an issue arise, we have dedicated teams to provide 24/7 coverage regarding outages, configuration matters, security issues, and so on. We have drilled procedures in place so that when an alert comes in, everyone knows what to do to ensure its prompt resolution.
Project data and isolation
Create multiple, byte-for-byte clones of production—securely and in isolation. You can clone your environments endlessly to meet your development workflows and know that these environments are isolated from all others—even your own. If your data needs to stay in a specific geographic region, you can specify where you want that to be.
Secrets management
Limit the secrets available on a specific environment, and override each value with a test value for non-production environments.
Geographic and project isolation
Every project is fully isolated from others. You can specify which region to host your project in, and we'll ensure that your data stays within that region.
Permissions and access management
Safeguard confidentiality, integrity, and availability. Retain complete control and governance of your application, while giving full flexibility to your developers to build, test, and deploy new features quickly.
Permissions per environment
Let developers freely and fearlessly create and work on test environments without worrying about changing or seeing production.
Goodbye passwords
SSH access is restricted to Public Key authentication only, ensuring only those who are supposed to log in, can.
Two-factor authentication
Any dashboard login can be enforced through a second authentication method.
Principle of least privilege
Permissions are set at minimum level and are managed through a central directory for terminations and audits.
Reduced attack surface
Our fully automated, reproducible build chain creates microcontainers, with no extraneous packages. This helps reduce the attack surface by having only what is strictly needed for your app and nothing else.
Hardened kernel and services
We run hardened Linux Kernels. All deployed packages come from signed internal repositories. We perform internal detection, logging, and alerting of any process or activity that attempts to break our infrastructure containment model.
Platform.sh provides a modern, secure infrastructure to provide you with peace of mind. We lock down access to the extent possible, while allowing you to specify your services and routes.
Rootless operations
Operations are performed without using root and are fully automated. All operations are logged.
Restricted access
SSH access is controlled per environment. All users are unprivileged.
Restrictive firewall
Our infrastructure employs both security groups and iptables firewalls. Only HTTP/S and SSH are allowed in. Services run in full network isolation. You specify the routes your application needs.
Read-only filesystem
When deployed on Platform.sh, user code is read-only so no unwanted changes can be made.
Multitier, secure, global managed CDN
Performance, security, and protection. We work with you to apply the best caching strategy to optimize your application performance, uptime, and costs—without compromising security. Our Enterprise offering gives you a solid foundation of vital security measures to protect your customers' personal information and other sensitive data.
DDoS mitigation
The CDN provides Distributed Denial of Service prevention.
Modern features
Your developers will love our additional modern features, like a built-in reverse proxy cache and TLS encryption on all connections.
99.99% uptime guarantee
This extends to the worldwide cache layer, so you can consistently deliver the best digital experience to your audiences.
 Switching to Platform.sh can help IT/DevOps organizations drive 219% ROI
Switching to Platform.sh can help IT/DevOps organizations drive 219% ROI Organizations, the ultimate way to manage your users and projects
Organizations, the ultimate way to manage your users and projects